In August 2012, Saudi Aramco—the largest oil company in the world—was hit with arguably the biggest hack in history. In addition to disrupting worldwide oil operations for months, the attack “bricked,” or rendered useless, some 35,000 endpoints. The replacement cost for those endpoints alone is estimated at over $50 million. The attack was perpetrated via a virus known as Shamoon.
The attack surface that was used: BIOS firmware
When I read this story, the part that caught my attention was the attack surface that was used: BIOS firmware. Specifically, Shamoon is designed to destroy computer hard drives by wiping the master boot record (MBR). The MBR is usually referred to as a boat loader and is used by the BIOS firmware to launch the operating system. If you delete the MBR, the firmware cannot launch the operating system and as a result you suddenly have a non-functional endpoint.
If your intention as a hacker is to render an endpoint useless, one of the easiest ways to achieve that is to disrupt the normal function of the BIOS firmware. Because, one of the key responsibilities of the firmware is to launch the OS and without an OS the endpoint becomes nothing more than an expensive paperweight. The group that wrote and deployed Shamoon certainly understood this fact and are perhaps the first hackers in history to intentionally target the normal operation of BIOS firmware as a means of attack. They certainly won’t be the last and this is where FirmGuard can help.

Hackers are Focused on BIOS Firmware
The use of an MBR is a relic of Legacy Boot and is no longer used (because it is vulnerable) with modern UEFI firmware. However, that doesn’t mean that endpoints that use legacy boot mode aren’t still in operation. In fact, they very much are, but how would you know? With FirmGuard, if any endpoint under management is in legacy boot mode you will be alerted immediately via the dashboard (see graphic below) and can then take remediation action, which often means just discarding the machine because it is likely very old.
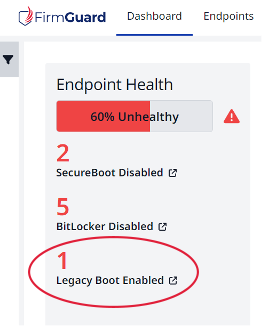
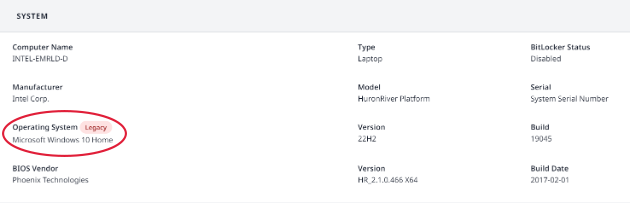
Hackers are continually shifting their tactics and BIOS firmware is clearly an attack surface they are focused on. In fact, the Cybersecurity and Infrastructure Security Agency (CISA) issued a very clear warning around UEFI firmware vulnerability in August, 2023. With FirmGuard in place, you can rest assured that the BIOS firmware layer of your (or your clients’) technology stack is secured and can prevent devasting attacks like Aramco from occurring.
To learn more about the types of BIOS firmware attacks that are out there in the wild, read this past blog post.