There’s a part of your infrastructure that probably isn’t getting the attention it deserves. It doesn’t live in the cloud. It doesn’t have a slick dashboard or constant notifications. But it’s the first thing that runs when your computer powers on. And if it’s compromised, every layer above it is instantly suspect.
I’m talking about BIOS. And more specifically, UEFI firmware.
For a long time, BIOS lived in the shadows. It was something you configured once during initial setup (maybe), updated manually if there was a serious issue (maybe), and otherwise ignored and hoped nothing went wrong. But that model doesn’t work anymore. Not with the way modern hackers operate, and not if you’re trying to take security seriously.
Firmware is no longer just a hardware thing. It’s an attack surface. And it’s time we started managing it like one.
BIOS: The Last Unmanaged Layer
Despite being foundational to trust, BIOS often sits outside the reach of typical security, patching, or configuration tools. It’s not that people don’t care – it’s that the tooling hasn’t kept up. And for attackers, that makes BIOS an ideal target.
Real-world threats like BlackLotus have made it clear that firmware persistence is real. Once an attacker lands in firmware, they can operate below the OS, evade detection, and survive reinstalls. That’s not a theoretical concern. It’s a hard reset of the security assumptions most organizations operate under.
But here’s the bigger issue: most MSPs and IT teams don’t have the ability to properly manage BIOS firmware at scale. Especially in multi-OEM environments, the lack of visibility, control, and integrity assurance is staggering.
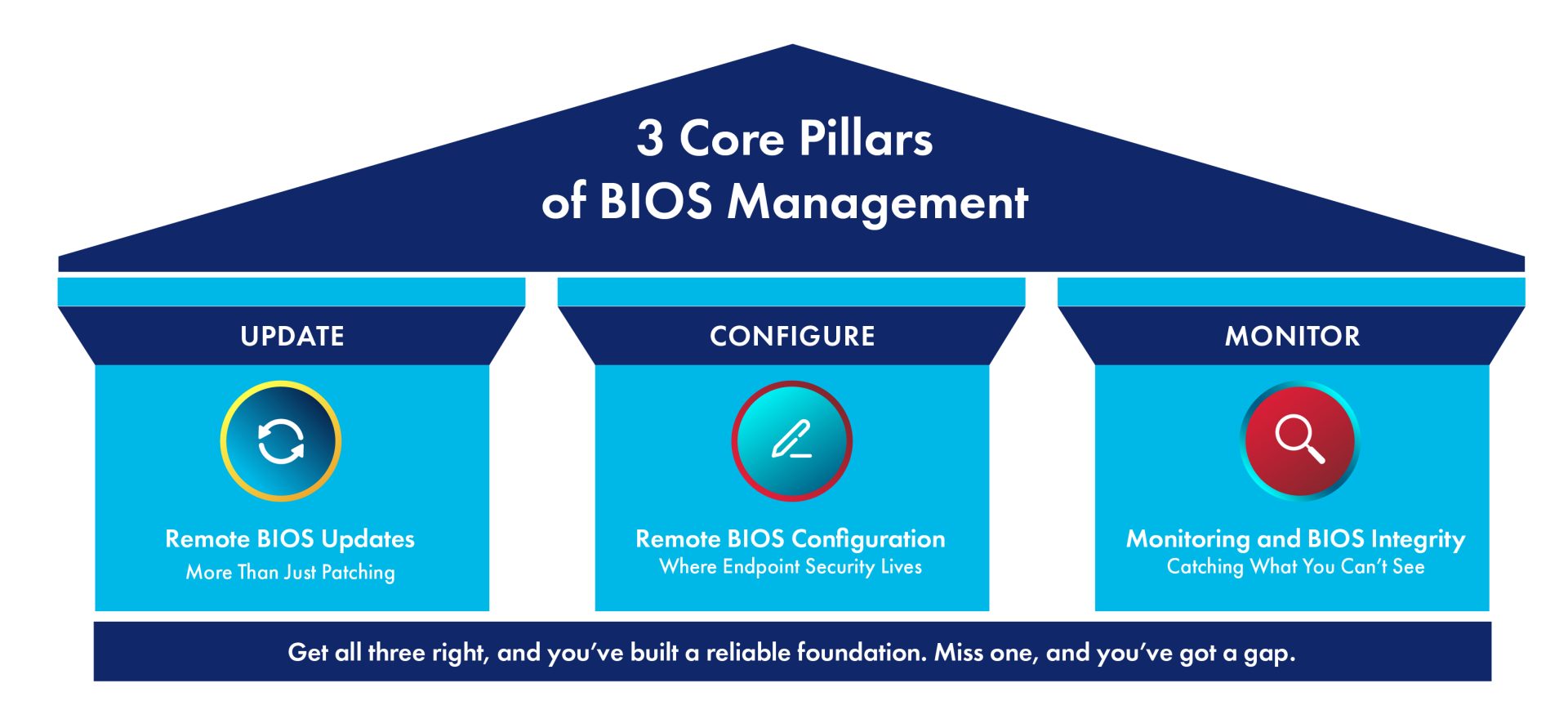
If we want to fix that, we need a model – something that’s operationally realistic but security-first. From our experience, effective BIOS management comes down to three core pillars:
- Secure update management
- Remote configuration enforcement
- Continuous monitoring and integrity verification
Get all three right, and you’ve built a reliable foundation. Miss one, and you’ve got a gap.
Pillar 1: Remote BIOS Updates... More Than Just Patching
Let’s be honest, BIOS updates aren’t fun. Every OEM has their own toolset; some updates require physical intervention, and there’s a real fear that you’ll brick a device. So, updates get delayed or skipped entirely.
That’s not just a nuisance. It’s a problem.
Old firmware leaves devices exposed to known vulnerabilities. Think of the Secure Boot bypasses that we’ve seen in the past few years. Many of those sat unpatched in the wild simply because there wasn’t a scalable way to apply updates.
And even when updates do happen, they often happen inconsistently. One endpoint is running BIOS version 1.2, another is on 1.4, and suddenly you’re chasing phantom hardware bugs caused by mismatches. Or worse, trying to roll out a new security feature only to find half your fleet can’t support it because the firmware is too old or not configured properly.
The fix? Centralized BIOS update management. That means:
- Always knowing at a glance which endpoints have out of date BIOS firmware
- Keeping an up-to-date inventory of firmware versions, across all endpoints, regardless of manufacturer
- Scheduling updates based on business risk and maintenance schedules
- Using delivery methods that don’t require someone to be physically present in front of a device
In short: Getting to a place where you know which firmware is running, and where, means you can quickly update firmware as required.
Pillar 2: Remote BIOS Configuration... Where Endpoint Security Lives
BIOS isn’t just low-level software. It can define the security capabilities of your endpoints and their hardware configuration. For example; if Secure Boot is off, if TPM is not active, you’re putting your device in unnecessary danger.
But here’s the catch: BIOS settings are rarely checked. Most IT teams assume they’re fine because “we configured them at imaging,” or they’re relying on spreadsheets and tribal knowledge. That’s not good enough anymore.
Settings drift. Firmware updates reset things. Field technicians toggle options to troubleshoot and forget to reset them. The result? Devices that quietly fall out of policy and open you up to both security and compliance risk.
Trying to manage this manually doesn’t scale. And traditional config tools like Microsoft SCCM or Intune, don’t really go deep enough to enforce BIOS settings. Especially not in multi-OEM environments.
So, what does good look like?
- Visibility into current BIOS configuration across all devices
- The ability to remotely change individual BIOS settings
- The ability to enforce (and re-enforce) policy remotely
The goal isn’t just standardization. It’s assurance. If you’re counting on Secure Boot or TPM for your endpoint protection strategy, you need to know those settings are enabled and locked.
Pillar 3: Monitoring and BIOS Integrity... Catching What You Can’t See
Even if your updates and configs are solid, you need to know when something changes. And BIOS changes do happen, whether intentionally or not.
The problem is that most security monitoring tools don’t touch firmware. Your EDR might be great at catching lateral movement or malware post-boot, but it’s blind to what happens before the OS even loads.
That’s where the real danger lies. A compromised BIOS can undermine everything, turning your trusted boot process into a lie, disabling controls silently, or hiding in a corner of your environment for months.
Runtime BIOS integrity checks are crucial. At a minimum, you want:
- TPM-backed measurements of firmware state (like PCRs)
- Alerts on unauthorized changes or drifts from known-good baselines
- Forensic visibility when something looks off at the firmware level
This kind of monitoring isn’t just about catching attacks. It’s also about trust. When your helpdesk says “we updated the firmware,” you want a way to verify it was done properly. When an auditor asks how you manage firmware risk, you want solid answers, not guesses.
Why All Three Pillars Matter
Each pillar on its own solves a real problem. But the real power comes from combining them.
You can’t trust monitoring data if your configurations aren’t enforced. You can’t enforce configs reliably if your firmware versions are all over the place. You can’t patch with confidence if you can’t verify what changed.
It’s all connected.
That’s why we need to stop treating BIOS as a one-off concern and start treating it as part of the broader endpoint security lifecycle. BIOS management isn’t just a project; it’s an operational discipline.
Final Thoughts: Bring BIOS Into the Fold
BIOS isn’t glamorous. It’s not a shiny new security product or a buzzword. But it’s foundational. And in the world we live in now, where firmware attacks are real, supply chain risk is tangible, and compliance frameworks are evolving, it can’t be left unmanaged.
If you’re serious about Zero Trust, endpoint hardening, or operational resilience, firmware has to be in the picture.
Start by asking the hard questions:
- Do we know what firmware is running across our devices?
- Can we remotely update or enforce BIOS settings we care about?
- Are we alerted when those settings change?
If the answer is “no” or “we think so,” that’s the signal. It’s time to start managing BIOS like the critical security layer it is.