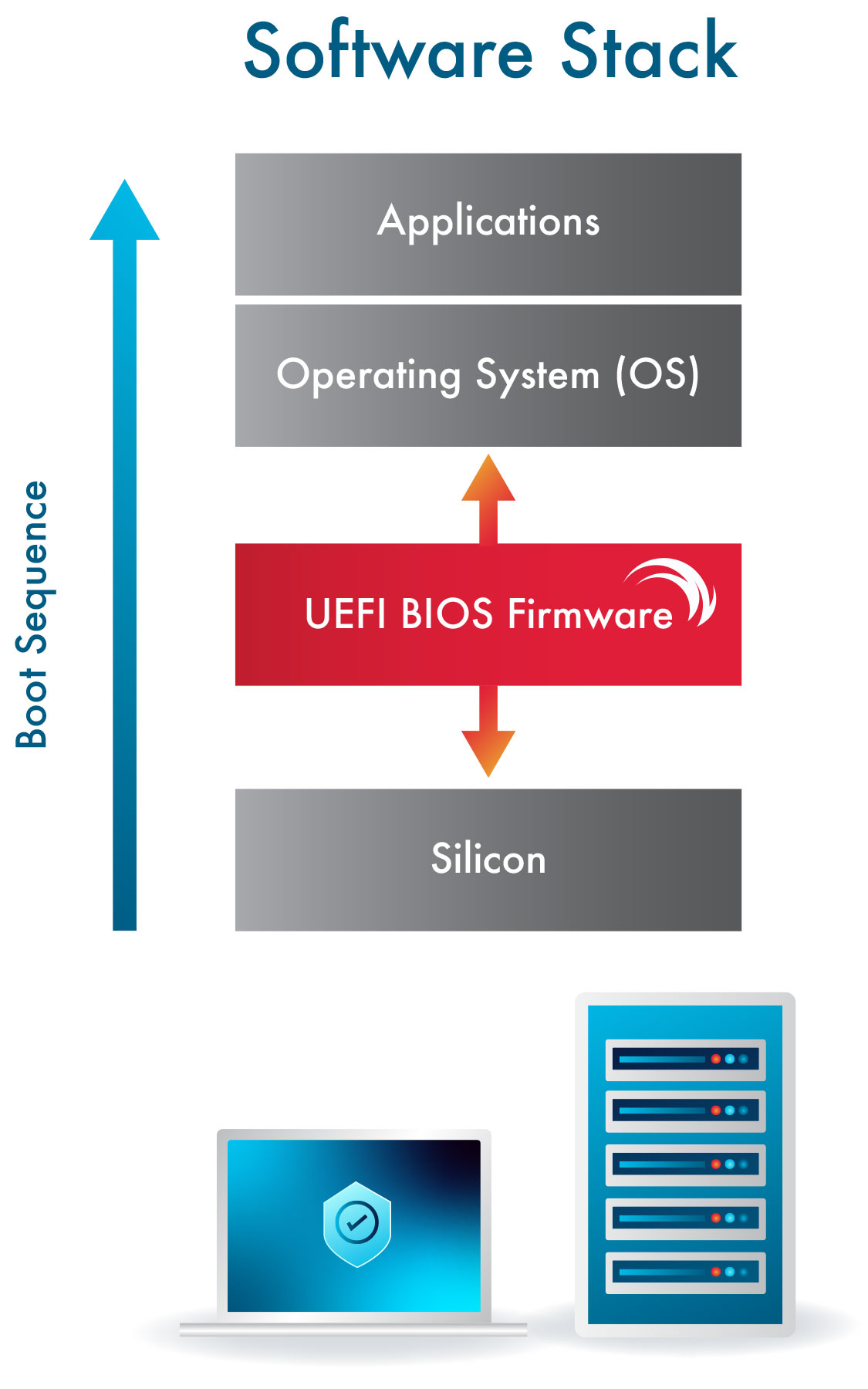
Firmware is the very first software that comes up when a device is powered on. It makes sure all the hardware and peripherals are functioning properly and then it launches the operating system. The figure shows firmware’s place in an endpoint’s tech stack. It has been commonly called BIOS, but modern firmware present in nearly all endpoints is based on the UEFI (Unified Extensible Firmware Interface) standard.
Without UEFI firmware, an endpoint would not be able to operate and would be nothing more than an expensive paperweight.
Given UEFI BIOS firmware’s critical position as the software that controls every component of an endpoint, it is not surprising that hackers target firmware with great intensity. By compromising a device’s firmware, a malicious actor can gain complete control of the machine including launching a rogue operating system. Furthermore, because UEFI firmware sits in its own dedicated flash memory on the motherboard, reinstalling the OS or even swapping out the hard drive will not rid the endpoint of infected firmware.
An attacker that hijacks firmware can easily eavesdrop, destroy or exfiltrate data, launch a rogue operating system or even render an endpoint inoperable.
The current industry focus on Zero Trust (ZT) should also encompass firmware, though many Zero Trust models and solutions do not. This is a mistake, as firmware is the root of trust for any endpoint. Since it is the first software loaded, compromised firmware can become an undetectable backdoor—an invisible gateway for implanting a rootkit to hijack the OS or network communications. From a ZT perspective, endpoint hardware should not trust firmware by default. Any serious discussions around ZT must include processes that regularly re-verify the firmware root of trust.
BIOS firmware security
Remote BIOS configuration
Remote BIOS update
Freeze endpoints until unlocked
Remote endpoint drive erasure
Remotely reimage an endpoint
Display endpoint system information
Monitor endpoint connectivity
Keep FirmGuard protected
Stay Connected with Pre-OS/No-OS Control via LAN or Wi-Fi